We demonstrate that it is possible to trigger Rowhammer bit flips on all DRAM devices today despite deployed mitigations on commodity off-the-shelf systems with little effort. This result has a significant impact on the system’s security as DRAM devices in the wild cannot easily be fixed, and previous work showed real-world Rowhammer attacks are practical, for example, in the browser using JavaScript, on smartphones, across VMs in the cloud, and even over the network.
Rowhammer is a vulnerability caused by leaking charges in DRAM cells that enables attackers to induce bit flips in DRAM memory. To stop Rowhammer, DRAM implements a mitigation known as Target Row Refresh (TRR). Our previous work showed that the new n-sided patterns can still trigger bit flips on 31% of today’s PC-DDR4 devices. We propose a new, highly effective approach for crafting non-uniform and frequency-based Rowhammer access patterns that can bypass TRR from standard PCs. We implement these patterns in our Rowhammer fuzzer named Blacksmith and show that it can bypass TRR on 100% of the PC-DDR4 DRAM devices in our test pool. Further, our work provides new insights on the deployed mitigations.
How did you do it?
We conducted a series of experiments starting from the observation that all previously used Rowhammer patterns such as single-sided, double-sided, and n-sided patterns (e.g., n=4) hammer aggressor uniformly, i.e., the same number of times.
| Fig. 1: Rowhammer access patterns from previous work. | Fig. 2: All existing patterns hammer aggressors uniformly. |
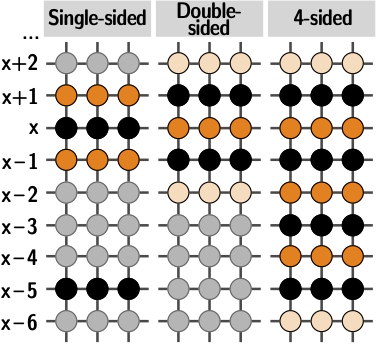 | 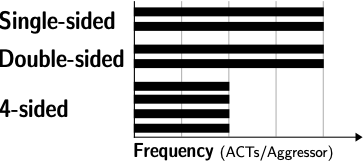 |
As the search space of non-uniform patterns is huge, we conducted a series of further experiments to determine the structure of patterns that effectively bypass TRR. Our experiments showed that the order, regularity, and intensity of accessing aggressor rows in non-uniform patterns are essential. We noticed that our observations nicely match with common parameters of the frequency domain, namely frequency, phase, and amplitude. We used these parameters to design frequency-based Rowhammer patterns that can effectively explore the space of non-uniform patterns. We implemented these patterns in a black-box fuzzer named Blacksmith that determines suitable parameter values crafting effective patterns targeting a specific device.
How bad is it?
For our evaluation, we considered a test pool of 40 DDR4 devices covering the three major manufacturers (Samsung, Micron, SK Hynix), including 4 devices that did not report their manufacturer. We let our Blacksmith fuzzer run for 12 hours to assess its capability to find effective patterns. Thereafter, we swept the best pattern (based on the number of total bit flips triggered) over a contiguous memory area of 256 MB and report the number of bit flips. The results in Table 1 show that our Blacksmith fuzzer is able to trigger bit flips on all 40 DRAM devices with a large number of bit flips, especially on devices of manufacturers A and D.
We also evaluated the exploitability of these bit flips based on three attacks from previous work: an attack targeting the page frame number of a page table entry (PTE) to pivot it to an attacker-controlled page table page, an attack on the RSA-2048 public key that allows recovering the associated private key used to authenticate to an SSH host, and an attack on the password verification logic of the sudoers.so library that enables gaining root privileges.
| DIMM | #Patterns | #Bit Flips | PTE | RSA-2048 | sudo | |||
|---|---|---|---|---|---|---|---|---|
| #Expl. BFs | Time | #Expl. BFs | Time | #Expl. BFs | Time | |||
| A0 | 47 | 82183 | 7604 | 4s | 210 | 30s | 17 | 5m |
| A1 | 116 | 12134 | — | — | 28 | 4m 12s | — | — |
| A2 | 462 | 134702 | 9198 | 6s | 306 | 21s | 13 | 6m 43s |
| A3 | 82 | 1746 | 73 | 2m 21s | 3 | 47m 37s | — | — |
| A4 | 460 | 5132 | 214 | 33s | 7 | 13m 16s | — | — |
| A5 | 42 | 113190 | 99 | 1m 27s | 269 | 34s | 12 | 11m 41s |
| A6 | 102 | 98425 | 52 | 2m 12s | 220 | 32s | 9 | 11m 55s |
| A7 | 66 | 32090 | 6043 | 6s | 69 | 2m 5s | 8 | 11m 11s |
| A8 | 83 | 92660 | 64 | 2m 24s | 184 | 54s | 15 | 10m 5s |
| A9 | 349 | 4889 | 136 | 28s | 6 | 9m 45s | — | — |
| A10 | 350 | 3051 | 216 | 24s | 7 | 12m 4s | — | — |
| A11 | 202 | 3171 | 197 | 2m 8s | 13 | 23m 21s | — | — |
| A12 | 74 | 43581 | 6596 | 7s | 116 | 55s | 2 | 38m 35s |
| A13 | 72 | 59721 | 4520 | 8s | 144 | 49s | 7 | 13m 44s |
| A14 | 51 | 64083 | 5172 | 8s | 151 | 44s | 7 | 14m 19s |
| A15 | 67 | 52580 | 4567 | 8s | 105 | 1m 3s | 7 | 14m 7s |
| A16 | 372 | 99552 | 6572 | 6s | 231 | 27s | 13 | 6m 30s |
| A17 | 425 | 138601 | 9775 | 3s | 324 | 11s | 10 | 5m 1s |
| A18 | 126 | 80601 | 11124 | 5s | 182 | 44s | 23 | 5m 28s |
| A19 | 107 | 11599 | 832 | 3s | 20 | 1m 18s | 3 | 6m 21s |
| B0 | 9 | 63 | — | — | — | — | — | — |
| B1 | 7 | 506 | 1 | 1h 44m* | 1 | 2h 31m* | — | — |
| B2 | 9 | 15 | — | — | — | — | — | — |
| B3 | 1 | 111 | 3 | 1h 16m | — | — | — | — |
| B4 | 101 | 1107 | 2 | 1h 27m | 4 | 34m 7s | — | — |
| B5 | 19 | 14 | — | — | — | — | — | — |
| B6 | 18 | 78 | — | — | — | — | — | — |
| B7 | 4 | 70 | — | — | — | — | — | — |
| B8 | 4 | 258 | — | — | 1 | 26m 50s* | — | — |
| B9 | 40 | 1223 | 3 | 1h 3m | — | — | — | — |
| C0 | 1 | 26 | 1 | 2h 8m* | — | — | — | — |
| C1 | 16 | 28 | — | — | — | — | — | — |
| C2 | 82 | 2551 | 1 | 1h* | 3 | 59m 39s | — | — |
| C3 | 6 | 636 | — | — | — | — | — | — |
| C4 | 31 | 769 | 4 | 59m 19s | 2 | 2h 5m | — | — |
| C5 | 23 | 1028 | — | — | 1 | 4h 2m* | — | — |
| D0 | 26 | 10646 | 5202 | 4s | 23 | 3m 43s | 4 | 19m 56s |
| D1 | 37 | 6655 | 4 | 19m 33s | 15 | 5m 25s | — | — |
| D2 | 3 | 2030 | 135 | 40s | 6 | 11m 41s | — | — |
| D3 | 41 | 6797 | 760 | 22s | 32 | 5m 49s | — | — |
Concluding, our work confirms that the DRAM vendors’ claims about Rowhammer protections are false and lure you into a false sense of security. All currently deployed mitigations are insufficient to fully protect against Rowhammer. Our novel patterns show that attackers can more easily exploit systems than previously assumed.
Demo
You can a demo of our Blacksmith fuzzer below, showing how easy and quick it is to find bit flips on TRR-enabled DDR4 devices. For the full details and more information about our work, please have a look at our paper, which is to appear at IEEE S&P 2022. You can find a recording of the S&P talk on YouTube.
FAQs
Following, we provide answers to the most frequently asked questions about our work.
- Are there any DIMMs that are safe?
We did not find any DIMMs that are completely safe. According to our data, some DIMMs are more vulnerable to our new Rowhammer patterns than others.
- Which implications do these new results have for me?
Triggering bit flips has become more easy on current DDR4 devices, which facilitates attacks. As DRAM devices in the wild cannot be updated, they will remain vulnerable for many years.
- How can I check whether my DRAM is vulnerable?
The code of our Blacksmith Rowhammer fuzzer, which you can use to assess your DRAM device for bit flips, is available on GitHub. We also have an early FPGA version of Blacksmith, and we are working with Google to fully integrate it into an open-source FPGA Rowhammer-testing platform.
- Why hasn’t JEDEC fixed this issue yet?
A very good question! By now we know, thanks to a better understanding, that solving Rowhammer is hard but not impossible. We believe that there is a lot of bureaucracy involved inside JEDEC that makes it very difficult.
- What if I have ECC-capable DIMMs?
Previous work showed that due to the large number of bit flips in current DDR4 devices, ECC cannot provide complete protection against Rowhammer but makes exploitation harder.
- What if my system runs with a double refresh rate?
Besides an increased performance overhead and power consumption, previous work (e.g., Mutlu et al. and Frigo et al.) showed that doubling the refresh rate is a weak solution not providing complete protection.
- Why did you anonymize the name of the memory vendors?
We were forced to anonymize the DRAM vendors of our evaluation. If you are a researcher, please get in touch with us to receive more information.
- Does Blacksmith work on DIMMs from other vendors?
According to statistics, the three DRAM chip manufacturers considered by us cover 94% of the DRAM market. However, we have tested Blacksmith on three DRAM devices from another vendor and we could successfully trigger bit flips on these devices too.
Disclosure
We have responsibly disclosed our results to affected parties. Following, we provide a short summary of the disclosure timeline.
- In Q1-2021, we initiated the responsible disclosure process with the National Cyber Security Centre Switzerland (NCSC-CH).
- In Q2-2021, NCSC informed major DRAM manufacturers, OEMs, and major tech companies about our findings and shared our paper’s draft and code.
- In Q3-2021, NCSC sent affected parties an updated version of our paper and communicated the public disclosure date.
- In Q4-2021, we received a CVE for our finding (CVE-2021-42114) and publicly disclosed Blacksmith on November 15, 2021.
The three DRAM manufacturers (Samsung, SK Hynix, and Micron), Intel, AMD, Microsoft, Oracle, and Google confirmed the reception of our findings. SK Hynix got in touch with us to discuss the LPDDR4X results. We discussed possible mitigations with Intel and our findings more in detail with Google.
The issues disclosed by this work are tracked under CVE-2021-42114.
Media Reception
Our findings were initially covered by an article in the ETH News and articles on Ars Technica and LifeWire. Later, international tech news picked up Blacksmith — for example, the EENews Europe, The Hacker News, The Register, ZDNet, BleepingComputer, SecurityWeek, TechXplore, techradar, Security Boulevard, Cyber Security News, and some other news sites (the Mac Observer, kiratas, Market Research Telecast, Hot Hardware, fudzilla). We also made it to the top position of the HN.
We noticed Blacksmith attracted media’s attention in Switzerland (Swiss Cyber Security News, SwissInfo, Volksblatt, Südostschweiz, Blick, Pilatus Today, msn), Germany (Heise, PCTipp, WinFuture), Italy (Hardware Upgrade), Greece (SecNews), Japan (Gigazine), Taiwan (iThome), and Russia (SecurityLab). Also, some blogs talked about Blacksmith, such as SecureBlink, MalwareTips, CyberFacts Weekly, Mac Pro Tricks, Cyware, and the German Born’s IT- und Windows Blog. We also observed a lot of tweets about Blacksmith on Twitter.
A few days after our public release, the well-known SecurityNow! podcast by Steve Gibson (Episode 845) and Bruce Schneier’s blog (Schneier on Security) featured Blacksmith too.
To the best of our knowledge, none of the affected vendors released an official statement. The only OEM who published a statement was Oracle on their blog. RedHat extended their existing knowledgebase article on DRAM-Related Faults by Blacksmith.
Acknowledgments
This research was supported by the Swiss National Science Foundation under NCCR Automation, grant agreement 51NF40_180545, and in part by the Netherlands Organisation for Scientific Research through grant NWO 016.Veni.192.262.

Errata
- 17.07.2021: We found a bug in one of our evaluation scripts, which affects the number of bit flips in the fuzzing column of the paper’s evaluation (Table II). The number of effective patterns and the total number of bit flips (collected during the sweep) remain the same. We updated the paper on our website. The previous version can be found here.
